GraphQL Access Control
Introspection separation
No, you don’t need to disable introspection. With RBAC Introspection separation, access control can be completely enforced at the edge. Users gain schema visibility only to allowed operations, types, and fields. Learn more about Inigo’s schema-based access control.
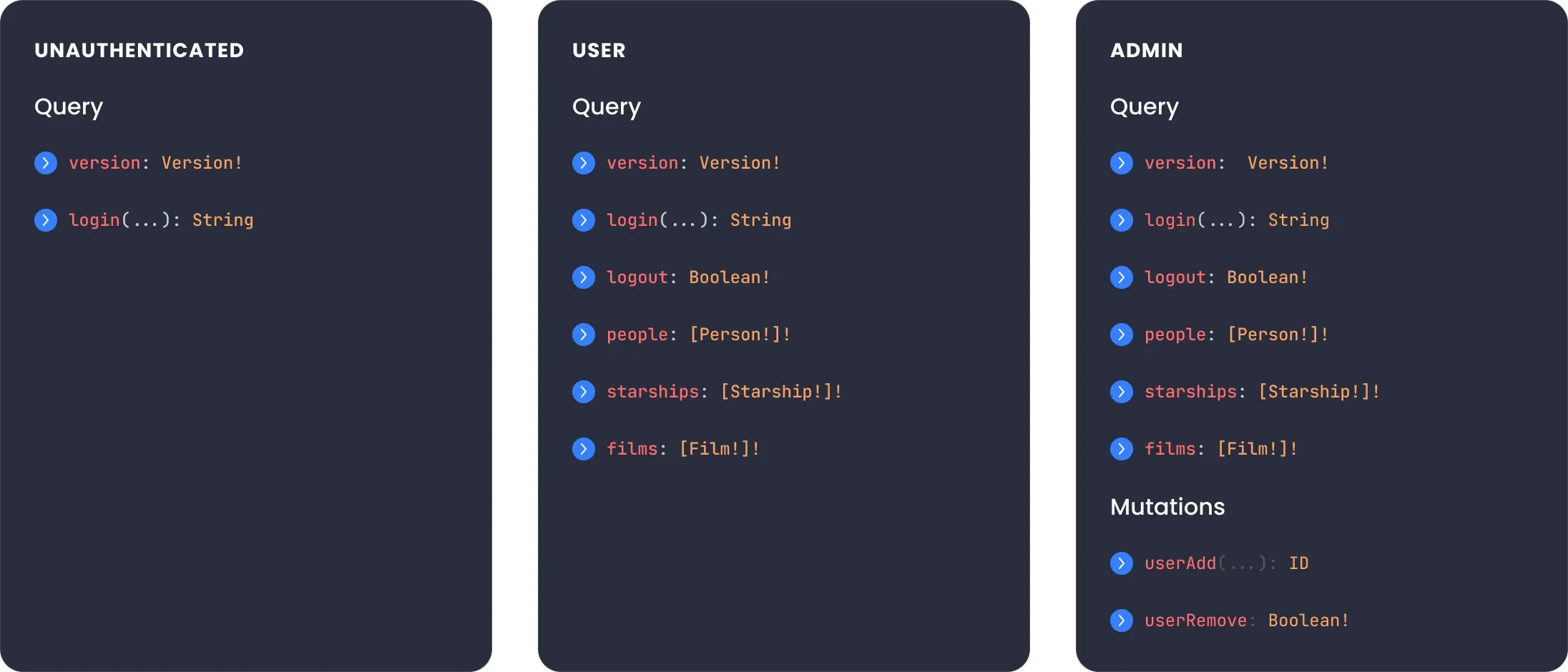
Schema-based access control
Keep resolvers clean and tight. Transform from complex code logic into role-based declarative configuration. Easy to maintain and manage during the development lifecycle.

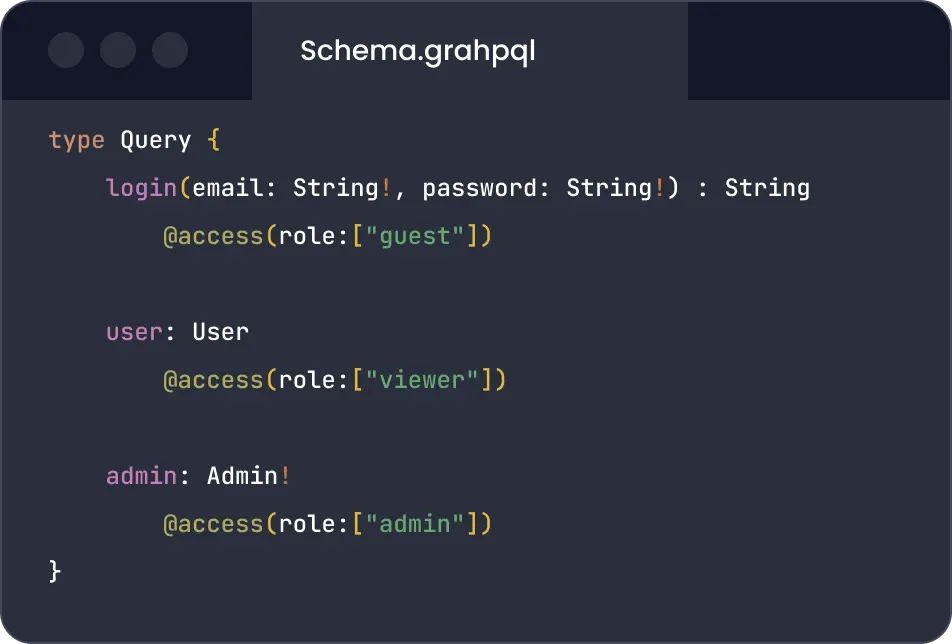
Directive approach
Apply RBAC directives to your GraphQL schema for fine-grained access control for authenticated and unauthenticated clients. Roles can be derived from a JWT token or HTTP headers.
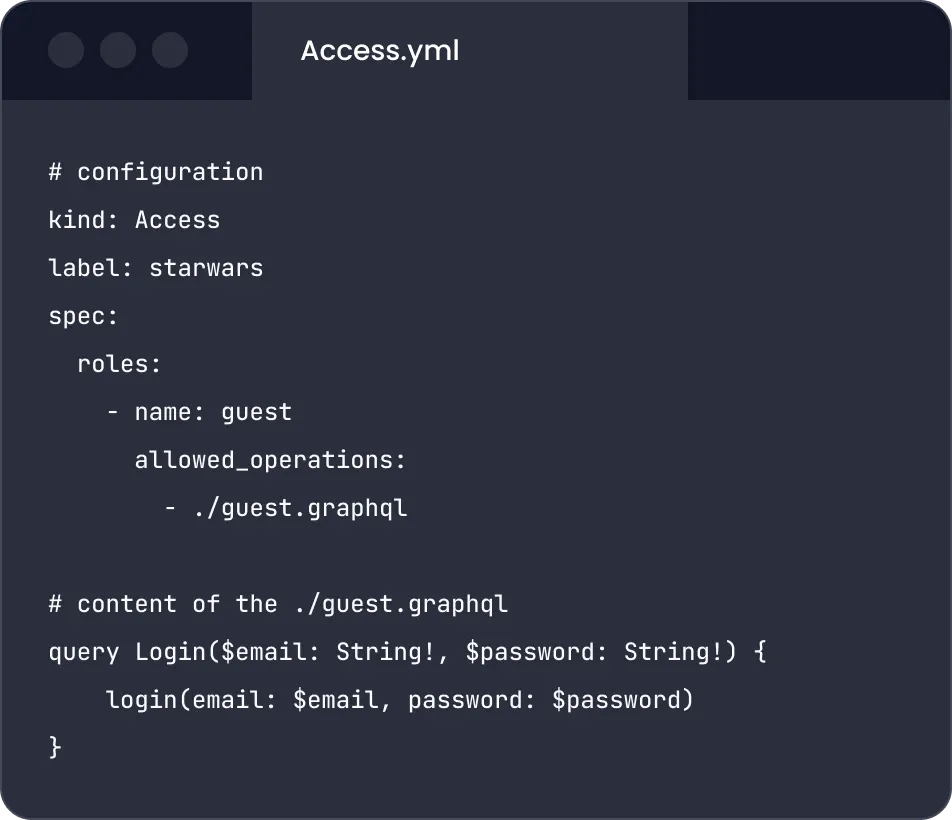
Allowlist approach
Define exactly what queries are allowed to be executed for your GraphQL API for a given role. This is useful for securing APIs that have a limited set of queries that clients should be able to run.
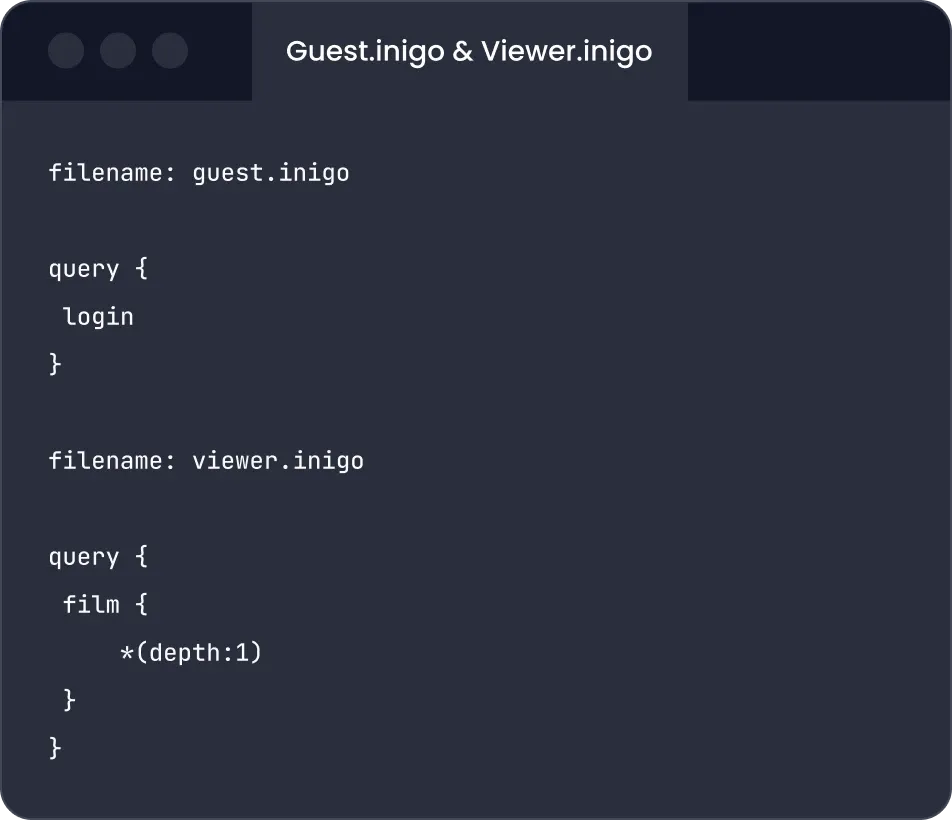
Schema subset approach
Limit access to types and fields in your schema for a given role. Queries will not be able to access unpermitted parts of the schema.