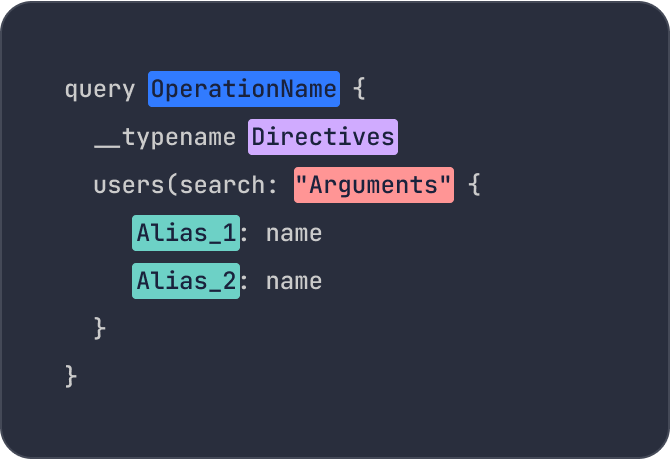
Protect Your API With Our Advanced GraphQL Security Features
Standard API gateways are blind to GraphQL attacks. Without purpose-built protection for GraphQL, API calls can be easily bypassed. This lack of sophisticated tooling has already led to high-profile DoS attacks and data leaks.
Stay ahead of the attackers that leverage GraphQL's free form nature to attack different phases in GraphQL's adoption journey from parser, resolver to business logic.
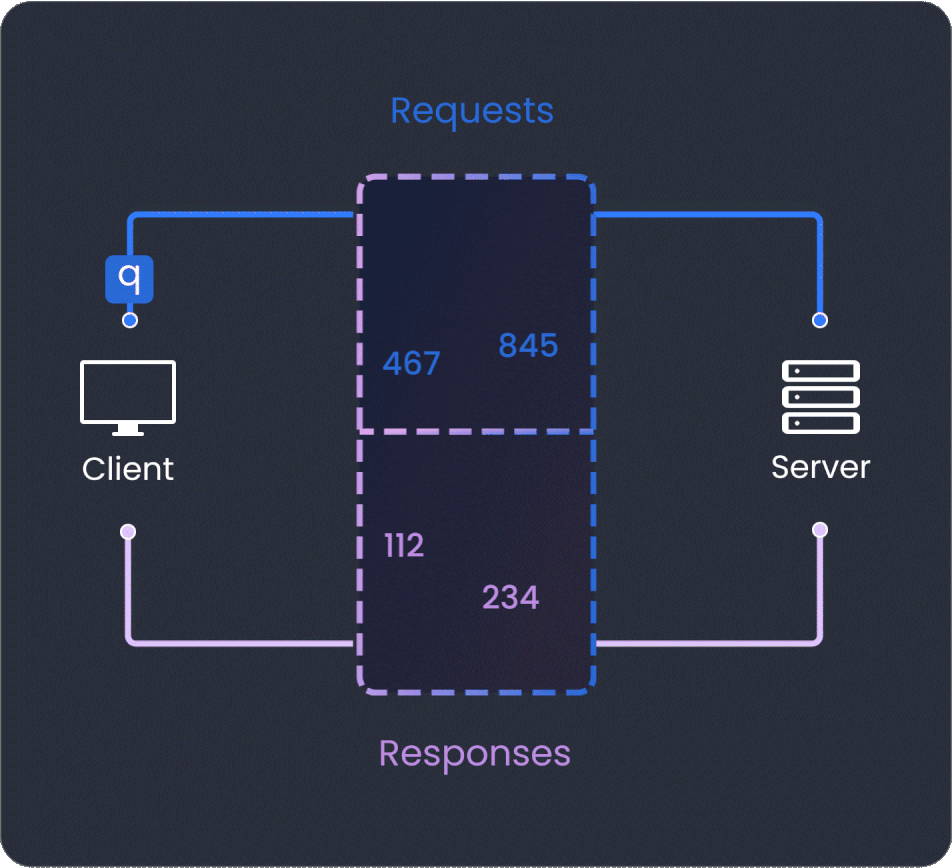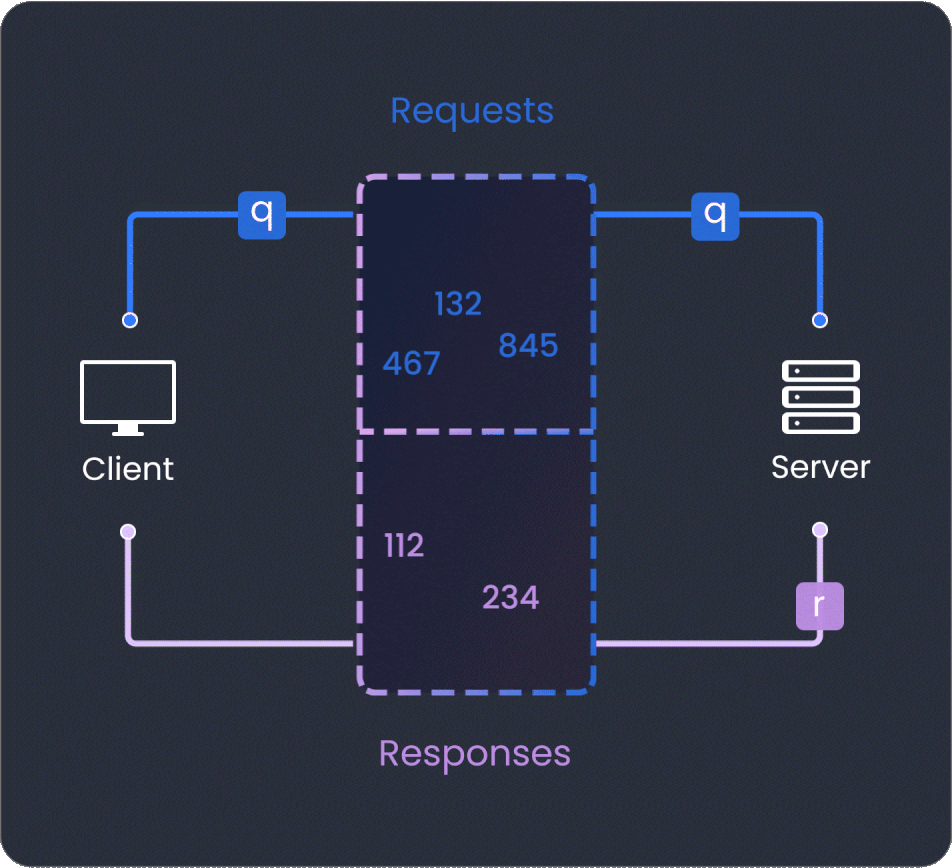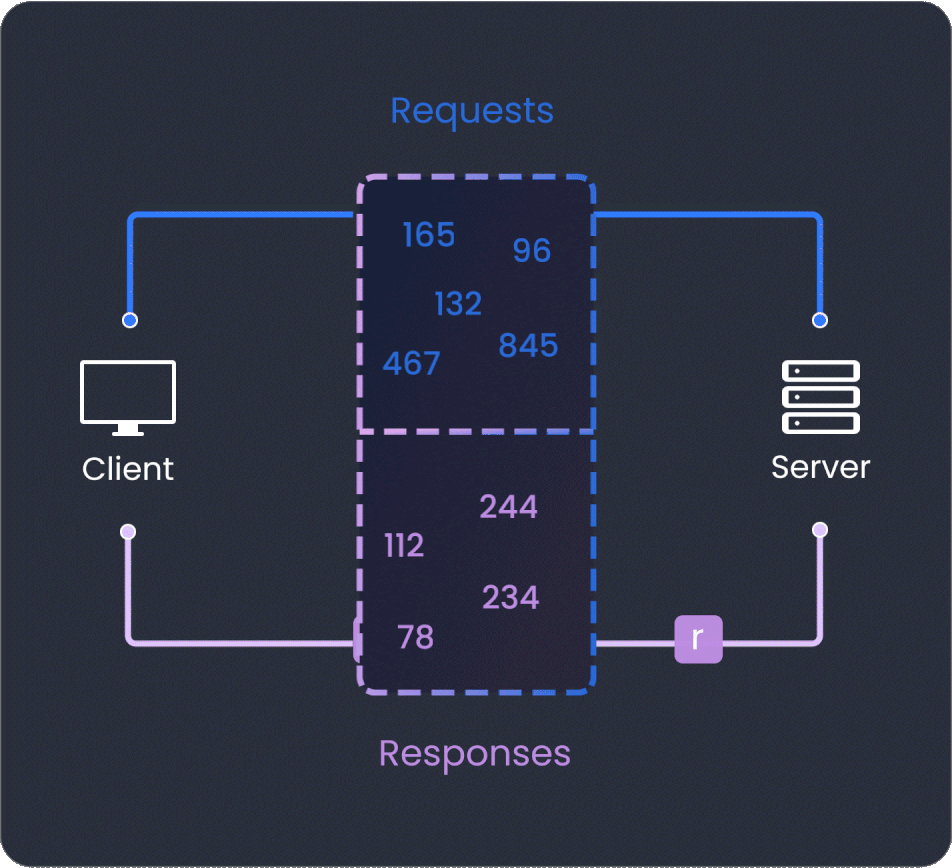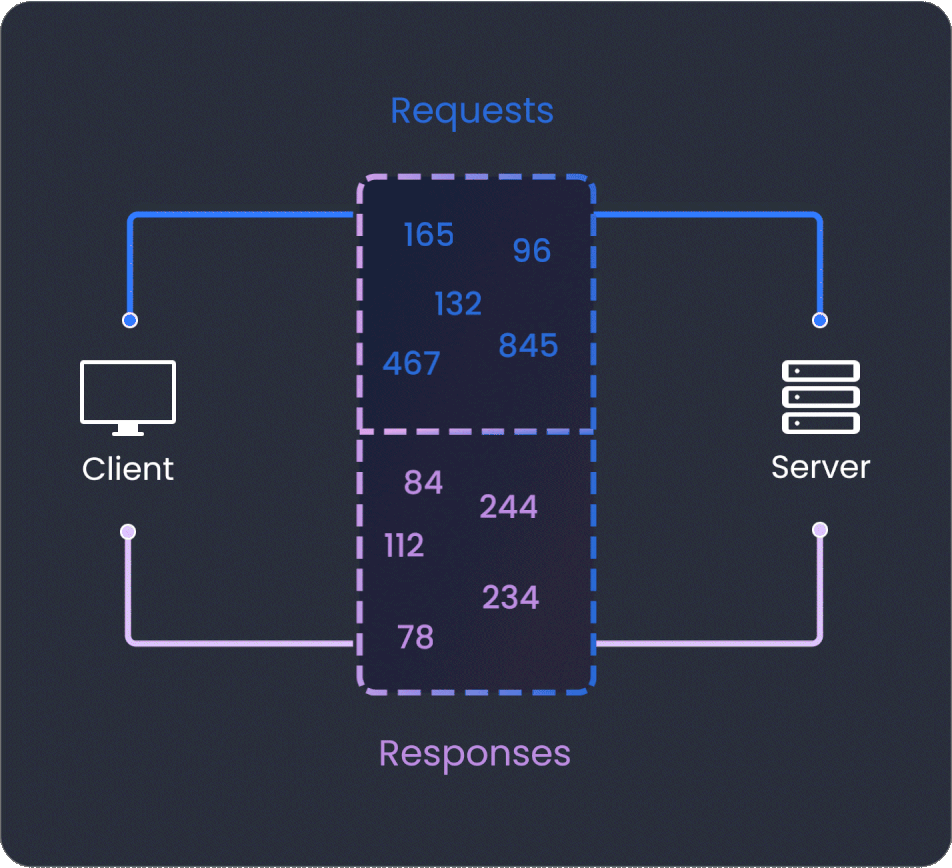
Rate limiting
Combine properly built field-level rate limiting and cost-based rate limiting to achieve comprehensive protection against DoS attacks and data leakage.
Limit the number of requests that can be made against specific operations and mutations. Analyze and evaluate each response to accurately any instances of data scraping or resource-heavy objects that could potentially cause an overload in your system
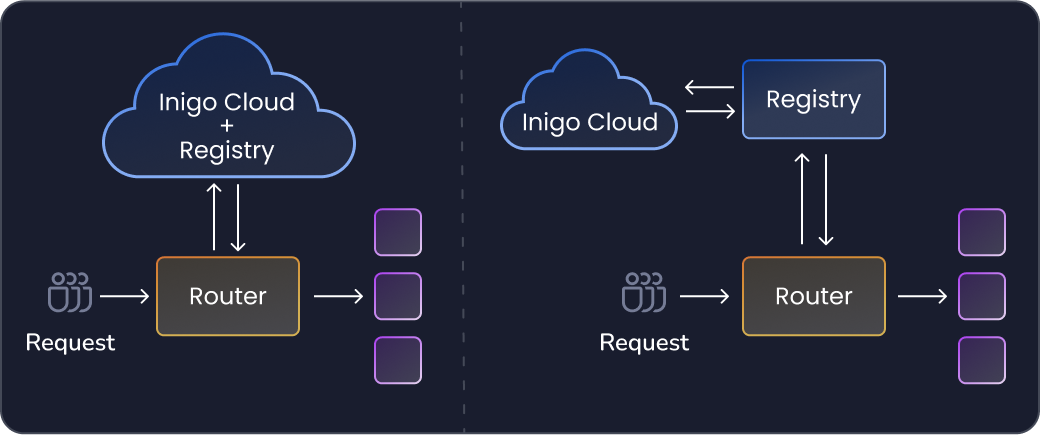
Operation registry
Operation Registry enhances GraphQL API security by permitting only pre-approved queries and mutations. It boosts performance and change management, while providing analytics for informed decision-making and fostering effective team collaboration.
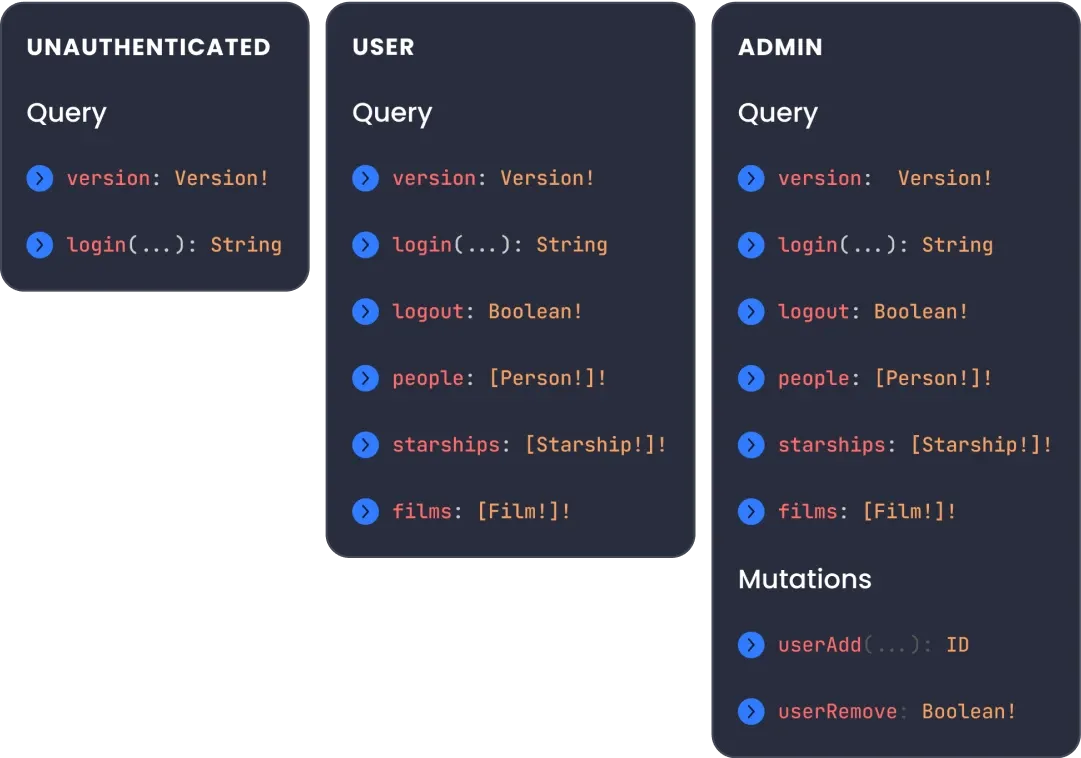
Secure introspection
With RBAC introspection separation, access control can be completely enforced at the edge. Users gain schema visibility only to allowed operations, types, and fields. Learn more about Inigo’s schema-based access control.
Keep resolvers clean and tight. Transform from complex code logic into role-based declarative configuration. Easy to maintain and manage during the development lifecycle.
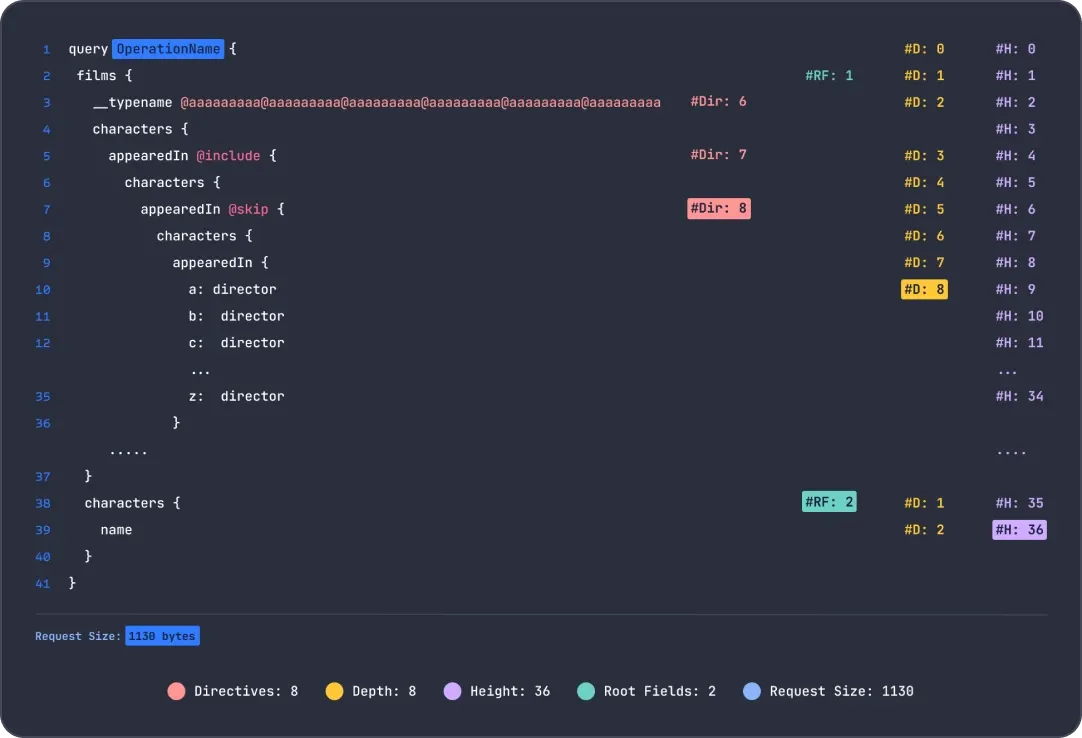
Query limits
GraphQL server implementations differ from each other. The strength of your choice of GraphQL server depends on those who maintain it. Attackers knows that. It is easy enough for an abuser to fingerprint your running implementing and work against it.
Ensure the right security knobs are in place to protect against query-based DoS attacks. Enforce tens to GraphQL controls to maintain operability.
Injection attacks
GraphQL’s complex payload expands attackers' ability to inject malicious payloads and compromise its underlying system. Properly validate and sanitize any user-supplied input in a GraphQL API to prevent injection attacks.