Analysis of public GraphQL vulnerability reports

Overview
One way to learn about GraphQL security is by analyzing public information related to vulnerabilities impacting GraphQL components such as GraphQL clients (like Relay) or GraphQL servers (like Apollo, Graphene, Ariadne, and even products like GitLab Enterprise, Magento, etc). We spent a few days examining data from two main sources: The CVE database by MITRE and the HackerOne Hacktivity portal to see what we can learn from analyzing vulnerability data.

GraphQL Vulnerability Data Analysis - MITRE CVE Database
The MITRE CVE database is the source of truth for CVEs. Before diving into the dataset, it’s important to highlight a few important things about the database:
- Not all vulnerabilities are reported.
- Not all vulnerabilities receive a CVE identifier.
- Some vulnerabilities are reported but never get a CVE identifier assigned.
The reason this is important to highlight is, while the CVE database is a good data sample, it is not a comprehensive list of vulnerabilities.
Generally speaking, vulnerabilities get a CVE identifier when either the vendor of the software impacted by the vulnerability or the researcher who found the flaw engages MITRE and files a CVE request. Some software vendors are authorized to issue their own software a CVE identifier, these vendors are acting as a CNA (CVE Numbering Authority) and you can find the list of CNA partners here, on this list you can find vendors such as GitLab, Adobe, GitHub, and more.
To get an idea of the GraphQL vulnerability dataset, we used the MITRE CVE database search option, where you can perform a free-text search. Here is what the search-term “GraphQL” brings up:
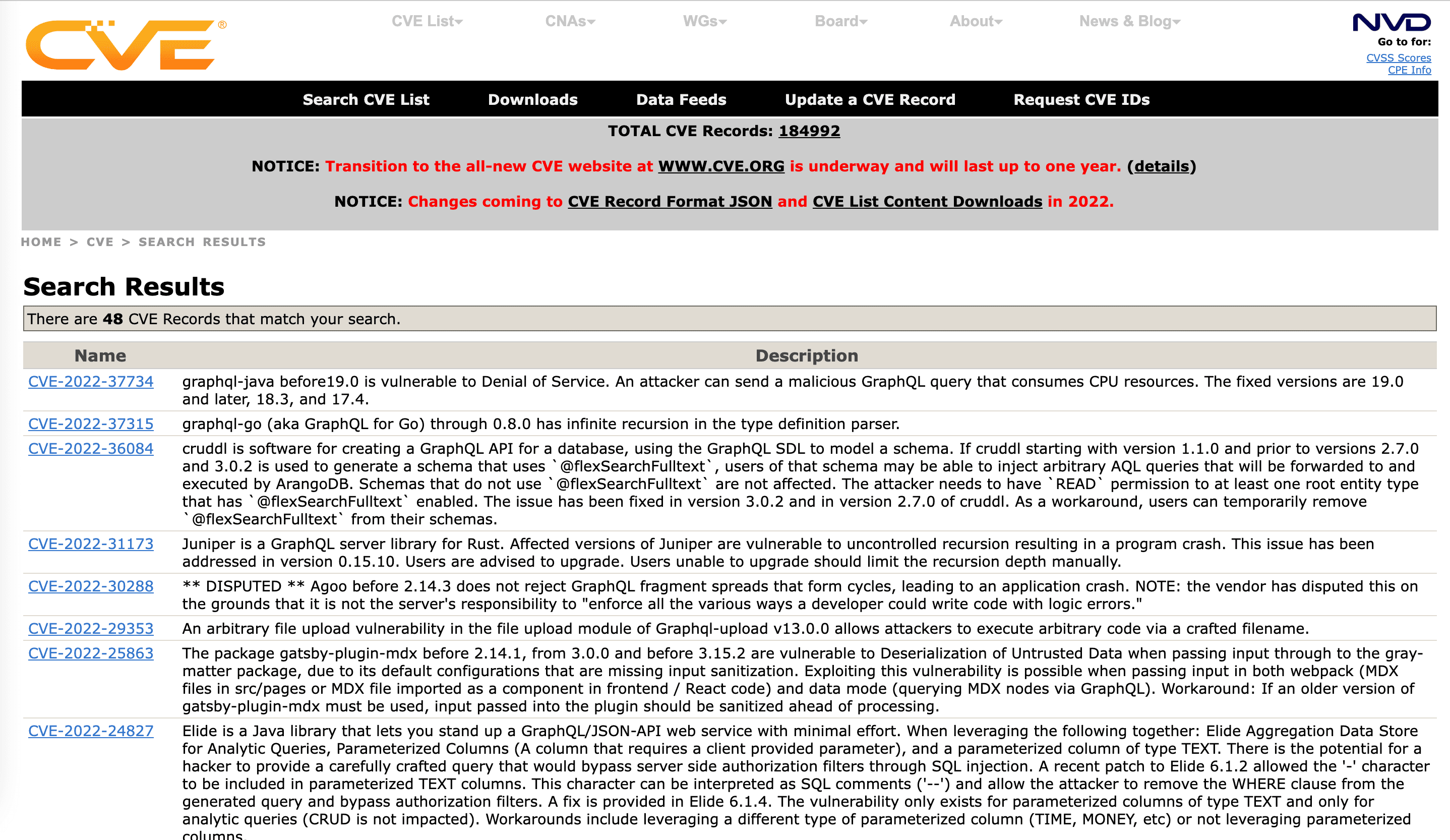
Having access to this dataset, a few questions came up:
- How many vulnerabilities are there with CVEs?
- What are the most common vulnerability classes?
- When was the first vulnerability tracked?
- Which GraphQL component has the most CVEs?
How many vulnerabilities are there with CVEs?
The search yielded a few dozen (45) CVEs related to GraphQL components, such as GraphQL servers, GraphQL client libraries, and so on.
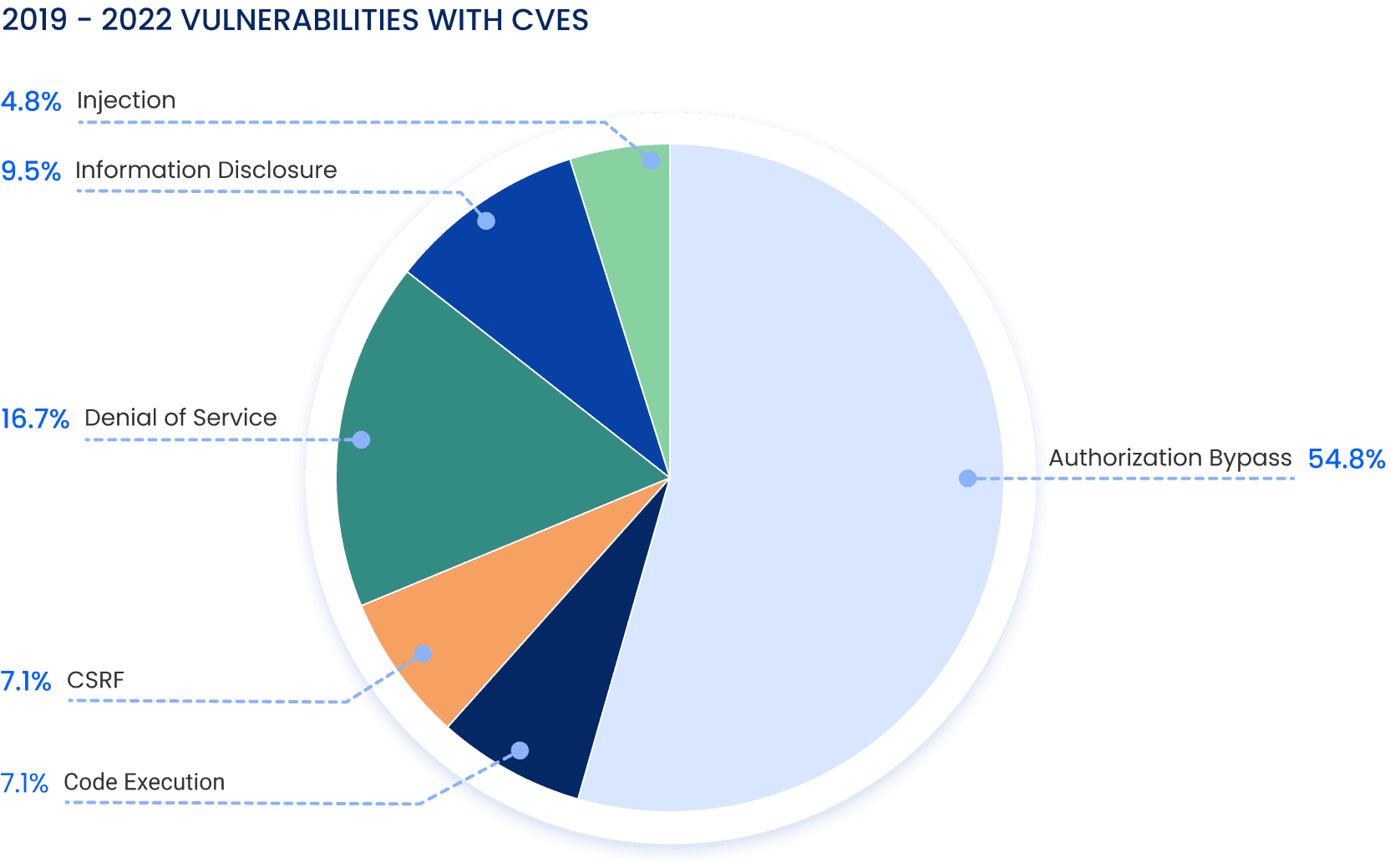
What are the most common GraphQL vulnerability classes?
Authorization (54%) and DoS-based (16%) vulnerabilities were the most popular vulnerability classes, as shown in the pie chart below.
When was the first vulnerability tracked?
Purely based on the CVE identifier strings, the oldest entry is from 2019 (CVE-2019-1000011) this is likely not the first ever vulnerability found in software with GraphQL, but it’s the oldest found in MITRE’s database.
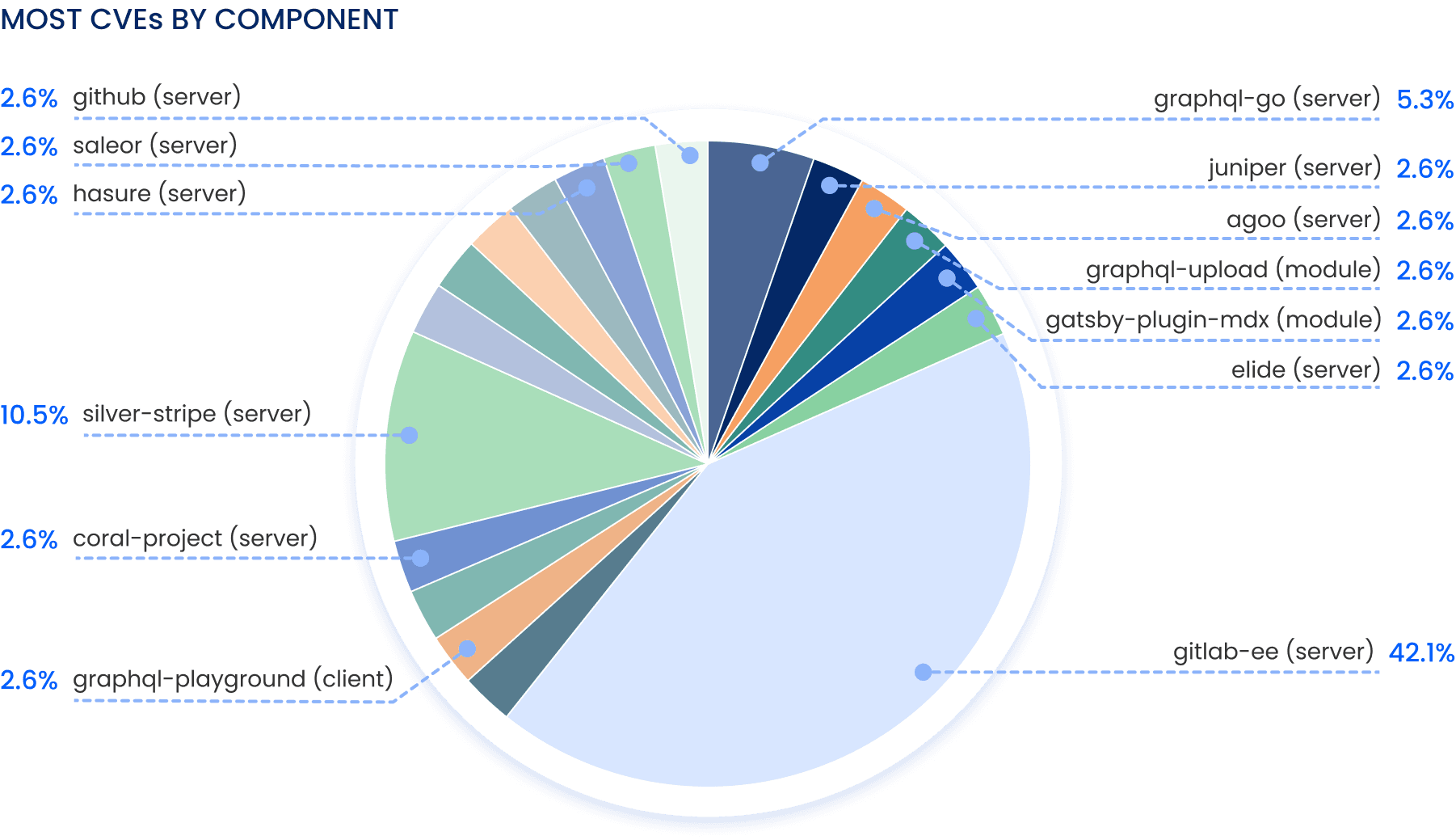
Which GraphQL software has the most CVEs?
This data is likely skewed by the popularity of the component itself, and is not indicative of how hardened a component is or is not, but nevertheless it is interesting data to analyze:
GraphQL Vulnerability Data Analysis - HackerOne
The HackerOne vulnerability database is a great resource to learn about the types of vulnerabilities researchers report on and get credited for. We performed a search against the public reports on HackerOne to see what types of vulnerabilities have been reported so far.
Since 2018, 74 vulnerabilities have been reported to various companies and bounties ranging anywhere from $250 to north of $20,000 were granted. Most vulnerabilities were in the category of Authorization flaws (87%), followed by DoS (7%) and others (5%)
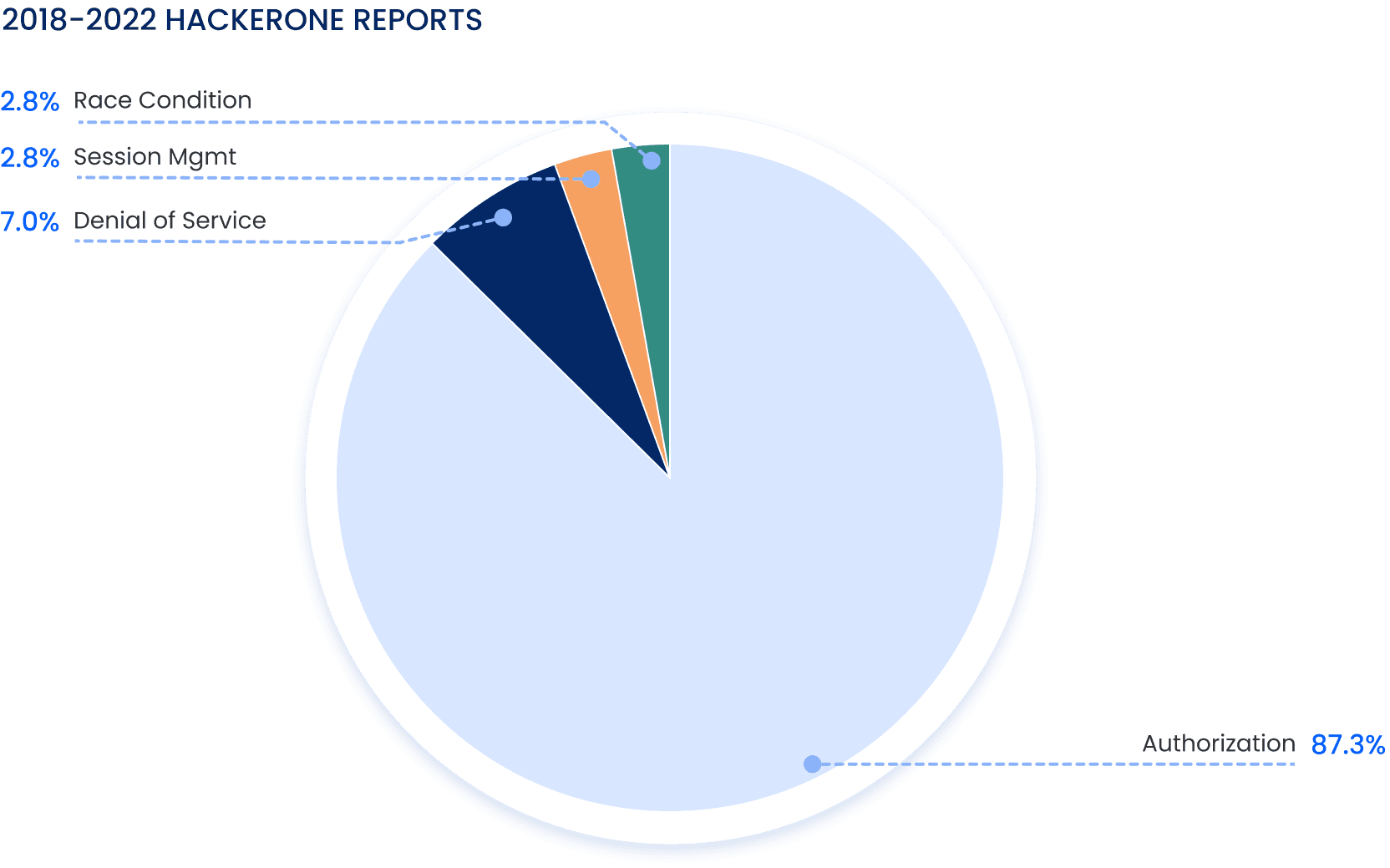
Security researchers participating in bug bounty programs are often motivated by money, and authorization-related vulnerabilities very often result in data leakages and impact to personal identifiable information (PII) - these vulnerabilities are considered to be the most critical to companies and the reward for finding such vulnerabilities is, as such, very incentivizing - so it comes as no surprise that most ethical hackers will test for authorization flaws before anything else.
One important fact about Bug Bounty programs is that testing for Denial of Service-based vulnerabilities is more often than not disallowed (and many times their bounties are also comparatively low where it is allowed), this is reflected in the chart by the limited number of reported DoS vulnerabilities.
GraphQL continues to be interesting both from an offensive as well as a defensive standpoint. Inigo’s GraphQL Security and Management solution helps address Authorization, Denial of Service, as well as other classes of vulnerabilities in GraphQL APIs.
Conclusion
GraphQL, with its free-form nature, introduces a new paradigm of attack surfaces. Inigo can help to put the proper guardrails in place, whether you are just starting or already have GraphQL in production. Learn more here.